endpoint protection small business
In today\’s digital age, small businesses are increasingly vulnerable to cyber threats that can jeopardize their operations, compromise sensitive data, and damage their reputation. Endpoint protection, a crucial component of cybersecurity, helps safeguard small businesses against a myriad of cyber risks. This article explores the significance of endpoint protection for small businesses, its key features, and best practices for implementation.
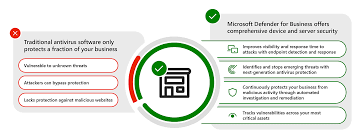
Understanding Endpoint Protection: Endpoint protection refers to a comprehensive security solution designed to protect endpoints such as computers, laptops, smartphones, and other devices connected to a network from cyber threats. These threats include malware, ransomware, phishing attacks, and other malicious activities aimed at exploiting vulnerabilities in endpoint devices. Endpoint protection solutions utilize a combination of antivirus software, firewalls, intrusion detection systems, and other advanced technologies to detect, prevent, and mitigate cyber threats in real-time.
Key Features of Endpoint Protection:
- Threat Detection and Prevention: Endpoint protection solutions employ advanced threat detection algorithms and signature-based scanning to identify and neutralize malicious software and activities before they can infiltrate the network or compromise sensitive data.
- Device Management: Endpoint protection platforms offer centralized device management capabilities, allowing small businesses to remotely monitor, configure, and update endpoint devices to ensure compliance with security policies and protocols.
- Data Encryption: Many endpoint protection solutions include data encryption features to protect sensitive information stored on endpoint devices from unauthorized access or theft.
- Patch Management: Endpoint protection software facilitates the timely installation of security patches and updates for operating systems and applications, reducing the risk of vulnerabilities being exploited by cyber attackers.
- Endpoint Detection and Response (EDR): Some advanced endpoint protection solutions include EDR capabilities, enabling small businesses to detect, investigate, and respond to security incidents in real-time, minimizing the impact of cyber attacks on their operations.
Best Practices for Endpoint Protection Implementation:
- Conduct a Security Assessment: Assess your small business\’s current cybersecurity posture, identify potential vulnerabilities, and determine the appropriate endpoint protection solution based on your specific needs and requirements.
- Implement Multi-Layered Security Measures: Deploy a multi-layered approach to endpoint protection that combines antivirus software, firewalls, email filtering, and web security to provide comprehensive defense against evolving cyber threats.
- Educate Employees: Train employees on cybersecurity best practices, including how to recognize and avoid phishing scams, securely handle sensitive information, and report suspicious activities to the IT department.
- Regularly Update and Maintain Endpoint Devices: Keep endpoint devices up-to-date with the latest security patches, software updates, and firmware upgrades to mitigate the risk of exploitation by cyber attackers.
- Monitor and Analyze Endpoint Activity: Continuously monitor endpoint devices for signs of unusual or suspicious activity, such as unauthorized access attempts, unusual network traffic, or malware infections, and respond promptly to mitigate potential security incidents.
Conclusion:
In conclusion, endpoint protection plays a crucial role in safeguarding small businesses against cyber threats by providing comprehensive security solutions tailored to the unique needs and challenges of endpoint devices. By implementing robust endpoint protection measures and following best practices for cybersecurity, small businesses can enhance their security posture, protect sensitive data, and mitigate the risk of cyber attacks, thereby safeguarding their reputation and ensuring continued business success.